Burp and iOS 9 App Transport Security
When trying to intercept an iOS 9 App’s traffic using Burp (or any other proxy software), you might run into issues caused by App Transport Security, a new security feature introduced in iOS 9.
By default, App Transport Security will cause most Apps on iOS 9 to only allow network connections to servers with a strong SSL configuration:
- TLS version 1.2
- Perfect forward secrecy cipher suites
- RSA 2048+ bits for the certificate chain
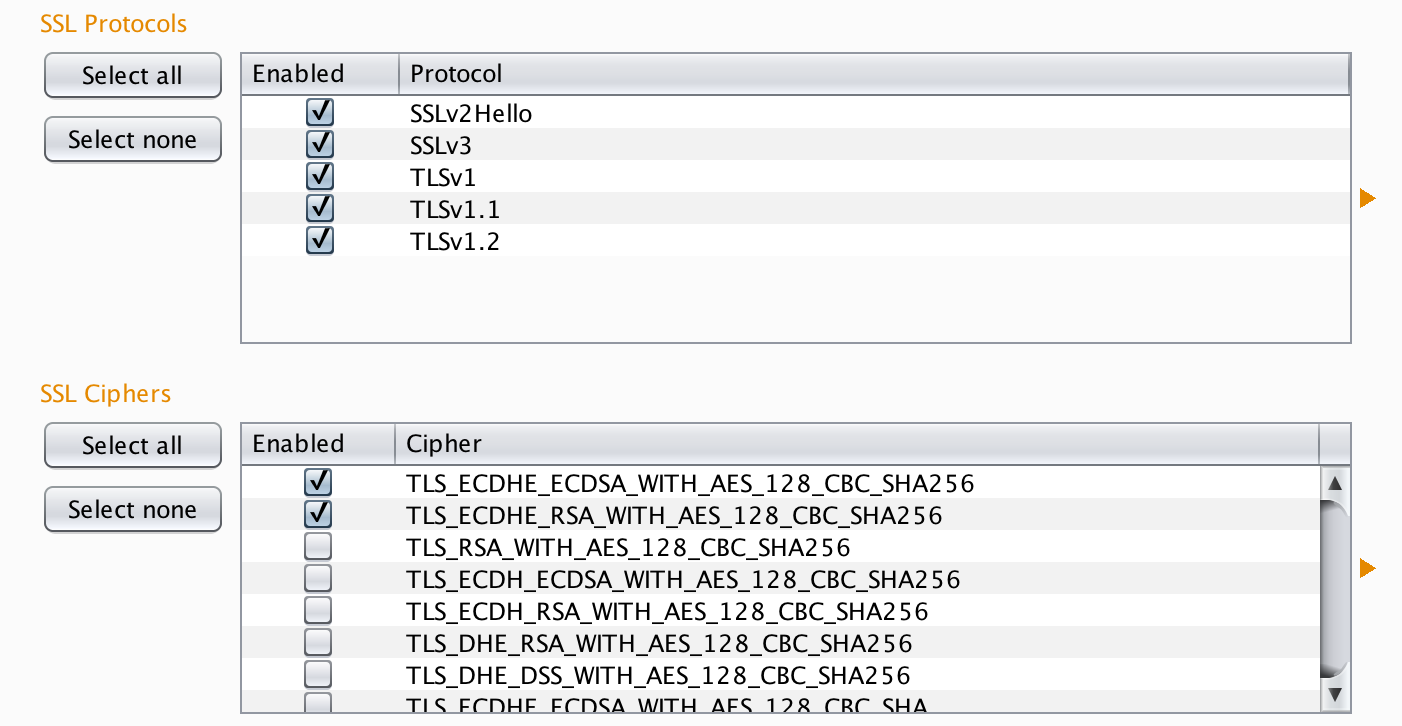
By default Burp does not support connections with these settings - TLS 1.2 is disabled by default - so most iOS 9 Apps will not be able to connect to Burp, when trying to proxy the App’s network traffic.
To address that, enable TLS 1.2 and the right cipher suites in Burp’s SSL settings:
Also, Burp’s default CA certificate is only 1024 bits, so you will have to generate a 2048 bits certificate and private key and import it into Burp (Proxy -> Options -> Import / Export CA certificate).

After updating Burp’s configuration and CA key pair, you should then be able to proxy iOS 9 Apps without any problem.